Enterprise Recon 2.14.0
SharePoint Online
From ER 2.14.0, you can use the Microsoft Graph implementation of Exchange Online by adding the SharePoint Online (Graph API) Target.
This section covers the following topics:
- SharePoint Online (Graph API)
- Licensing
- Requirements
- Configure Authentication Credentials
- Set Up and Scan a SharePoint Online (Graph API) Target
- Edit SharePoint Online (Graph API) Target Path
- Unsupported Types and Folders in SharePoint Online (Graph API)
- Deleted SharePoint Online Sites
- SharePoint Online (Graph API) Remediation
- Unsupported Remediation Locations in SharePoint Online
- SharePoint Online (Legacy)
SharePoint Online (Graph API)
Licensing
For Sitewide Licenses, all scanned SharePoint Online Targets consume data from the Sitewide License data allowance limit.
For Non-Sitewide Licenses, SharePoint Online Targets require Server & DB Licenses, and consume data from the Server & DB License data allowance limit.
See Target Licenses for more information.
Requirements
| Component | Description |
|---|---|
| Proxy Agent | 2.14.0 Agent
Recommended Proxy Agents:
|
| TCP Allowed Connections | Port 443 for cloud services. |
Configure Authentication Credentials
To be able to add and scan SharePoint Target, you must configure the credentials you want Enterprise Recon to use to connect to your SharePoint account.
- Generate Client ID and Tenant ID Key
- Generate Client Secret Key or
Generate a Client Certificate for authentication.
To be able to probe, scan, and remediate list item attachments, authenticate with client certificates.
- Grant API Access
Generate Client ID and Tenant ID Key
- With your administrator account, log in to the Azure app registration portal.
- In the App registrations page, click + New registration.
-
In the Register an application page, fill in the following fields:
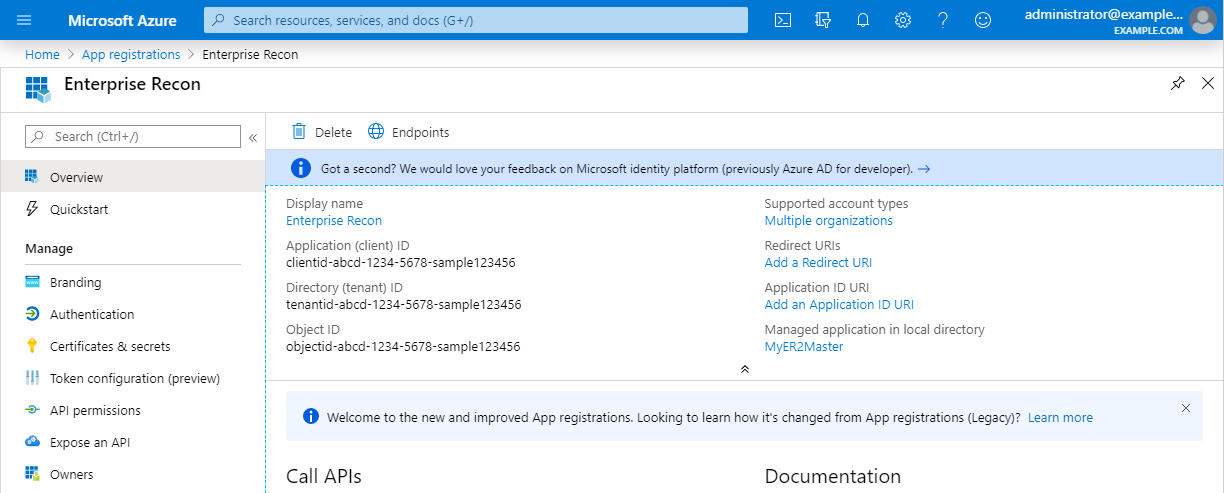
Field Description Name Enter a descriptive display name for ER2. For example, Enterprise Recon. Supported account types Select Accounts in this organizational directory only. - Click Register. You will be redirected to the Overview page for the newly registered app, Enterprise Recon.
-
Take down the Application (client) ID and Directory (tenant) ID. This is required when you want to Set Up and Scan a SharePoint Online (Graph API) Target.
Generate Client Secret Key
- With your administrator account, log in to the Azure app registration portal.
- In the App registrations page, go to the Owned applications tab. Click on the app that you registered (e.g. Enterprise Recon) when generating the Client ID and Tenant ID key.
- In the Manage panel, click Certificates & secrets.
- In the Client secrets section, click + New client secret.
-
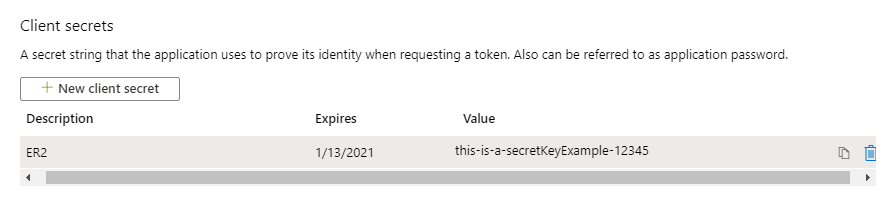
In the Add a client secret page, fill in the following fields:
Field Description Description Enter a descriptive label for the Client Secret key. Expires Select a validity period for the Client Secret key. -
Click Add. The Value column will contain the Client Secret key.
-
Copy and save the Client Secret key to a secure location. This is required when you want to Set Up and Scan a SharePoint Online (Graph API) Target.
Save your Client Secret key in a secure location. You cannot access this Client Secret key once you navigate away from the page.
Generate a Client Certificate
-
Obtain Signed SSL Certificate or generate a self-signed certificate by running the following commands:
# Generate a new private key with passphrase # Syntax: openssl genrsa -aes256 -out <private-key-filename>.pem 2048 openssl genrsa -aes256 -out private-key.pem 2048 Alternative: Generate a new private key without passphrase openssl genrsa -out private-key.pem 2048
# Generate certificate and provide the details for the certificate when prompted # Where <private-key-file> is the newly generated private key from the previous command # Syntax: openssl req -new -x509 -sha256 -days 365 -key <private-key>.pem -out <public-cert-filename>.pem openssl req -new -x509 -sha256 -days 365 -key private-key.pem -out public-cert.pemThe SSL certificate and the private key must be PEM files. If in different format, please convert them to .pem format before proceeding. - Upload the certificate to your registered application.
- With your administrator account, log in to the Azure app registration portal.
- In the App registrations page, go to the Owned applications tab.
- Click on the app that you registered (e.g. Enterprise Recon) when generating the Client ID and Tenant ID key.
- In the Manage panel, click Certificates & secrets.
- In the Certificates section, click Upload certificate.
- From the dropdown, select your certificate in PEM format.
- In the Description field, enter a description for the certificate.
- Click Add.
-
In the same folder as your certificate, run the command below to view the x5t#S256 value of the certificate:
# Where <public-cert> is the newly generated certificate in step 1 above printf ‘x5t#S256: %s\n’ “$(openssl x509 -in public-cert.pem -inform PEM -outform DER | openssl dgst -sha256 -binary | openssl base64 -e | tr -d ‘\n’ | tr ‘/+’ ‘_-‘ | tr -d ‘=’)”This displays the x5t#S256 value of your certificate.# Displays value in the format of # x5t#S256: <value> x5t#S256: aBcDeFGHiJKLMA1NOPQR_wxYzd-x5t#S256value - Take down the displayed x5t#S256 value. The x5t#S256 value and the private key PEM file are required when you want to Set Up and Scan a SharePoint Online (Graph API) Target (authenticated via Client Certificate).
Grant API Access
To scan SharePoint Online Targets, you will need to grant ER2 permissions to access specific resource APIs.
- With your administrator account, log in to the Azure app registration portal.
- In the App registrations page, go to the Owned applications tab. Click on the app that you registered (e.g. Enterprise Recon) when generating the Client ID and Tenant ID key.
- In the Manage panel, click API permissions.
- In the Configured permissions section, click + Add a permission.
- In the Request API permissions page, select Microsoft Graph > Application permissions.
-
Select the following permissions for the registered app (e.g., Enterprise Recon):
API Permissions Description - Sites.Read.All
Required for probing and scanning SharePoint Online (Graph API) Targets (except list item attachments). - Sites.ReadWrite.All
- Sites.Manage.All
Required for remediating SharePoint Online (Graph API) Targets (except list item attachments). Recommended Least Privilege User ApproachTo reduce the risk of data loss or privileged account abuse, the required permissions in the table above for scanning and/or remediating SharePoint Online Targets are based on the recommended least privilege user approach. This could cause some paths (e.g., _catalogs/solutions) to be logged as inaccessible locations.
To scan these locations, select the Sites.FullControl.All permission for Microsoft Graph API.
Never grant full user access privileges or unrestricted data access to any application if it is not required.
- Click Add permissions.
- In the Configured permissions page, click on Grant admin consent for <organization name>.
-
In the Grant admin consent confirmation dialog, click Yes. The Status column for all the newly added API permissions will be updated to "Granted for <organization name>".
- (Required only if
authenticating SharePoint Online using a client certificate to scan and
remediate the list item attachments) Back to the
API Permissions > Request API Permissions page,
select SharePoint > Application permissions.
-
Select the following permissions for the registered app (.e.g, Enterprise Recon):
API Permissions Description - Sites.Read.All
- Sites.ReadWrite.All
Required for probing list item attachments in SharePoint Online (Graph API) Targets. - Sites.FullControl.All
Required for scanning and remediating list item attachments in SharePoint Online (Graph API) Targets. - Click Add permissions.
- In the Configured permissions page, click on Grant admin consent for<organization name>.
- In the Grant admin consent confirmation dialog, click Yes. The Status column for all the newly added API permissions will be updated to "Granted for <organization name>".
-
Set Up and Scan a SharePoint Online (Graph API) Target
To add a SharePoint Online Target:
- From the New Scan page, Add Targets.
- In the Select Target Type dialog box, select Microsoft 365 > SharePoint Online.
- Fill in the following fields:
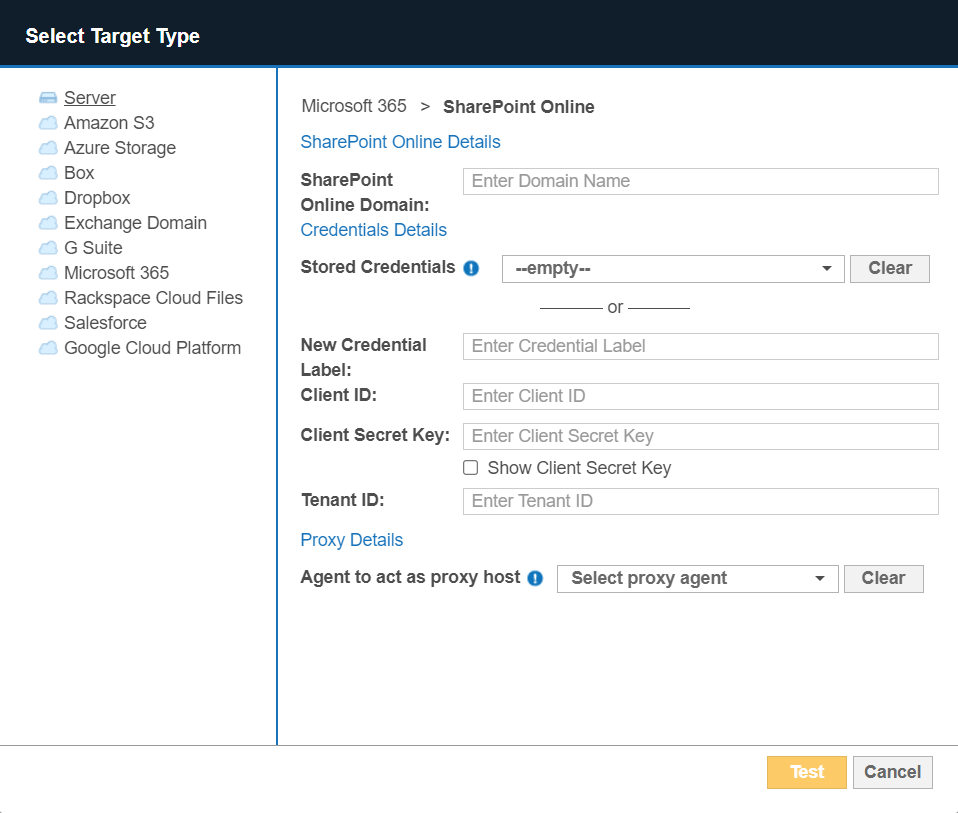
Field Description SharePoint Online Domain Enter your SharePoint Online organization name.
For example, if you access SharePoint Online at https://mycompany.sharepoint.com, enter mycompany.
New Credential Label Enter a descriptive label for the SharePoint Online credential set.
Tenant ID Enter the Tenant ID key for the registered app. Example: tenantid-1234-abcd-5678-02011df316f4
See Generate Client ID and Tenant ID Key for more information.
Client ID Enter the Client ID for the registered app.
Example: clientid-1234-5678-abcd-6d05bf28c2bf
See Generate Client ID and Tenant ID Key for more information.
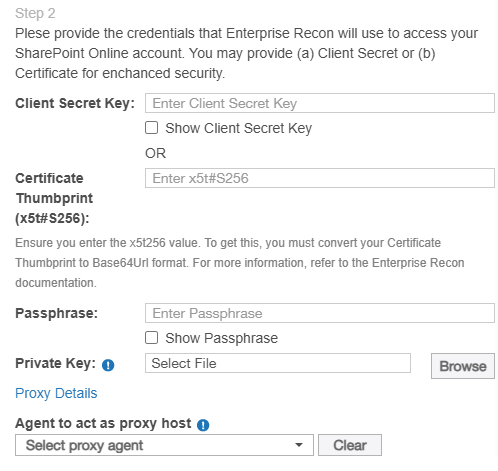
Authentication credentials (client secret or client certificate) Provide the credentials that Enterprise Recon will use to access your SharePoint Online account. You may provide either the (i) Client Secret or the (ii) Client Certificate, but not both.
- To use the Client Secret Key, in the Client Secret Key
field, enter the Client Secret key generated for the registered
app.
Example: client~secret.key-CHvV1B5YQfr~6zDjEyv
See Generate Client Secret Key for more information.
- To use the client certificate, perform the following steps:
- In the Certificate Thumbprint (x5t#S256) field,
enter the x5t#S256 value you have saved for the registered
app.
Example: aBcDeFGHiJKLMA1NOPQR_wxYzd-x5t#S256value
See Generate a Client Certificate for more information.
- (Required if the private key file is encrypted) In the Passphrase field, enter the passphrase for your private key file.
- In the Private Key field, upload the private key
(*.pem) file.
If the private key file is encrypted, please ensure you have provided the passphrase in the Passphrase field.
- In the Certificate Thumbprint (x5t#S256) field,
enter the x5t#S256 value you have saved for the registered
app.
Agent to act as proxy host Select a supported Proxy Agent host with direct Internet access. Recommended Least Privilege User ApproachData discovery or scanning of data requires read access. Remediation actions that act directly on supported file systems including Delete Permanently, Quarantine, Encryption and Masking require write access in order to change, delete and overwrite data.
To reduce the risk of data loss or privileged account abuse, the Target credentials provided for the intended Target should only be granted read-only access to the exact resources and data that require scanning. Never grant full user access privileges or unrestricted data access to any application if it is not required.
- To use the Client Secret Key, in the Client Secret Key
field, enter the Client Secret key generated for the registered
app.
- Click Test. If ER2 can connect to the Target, the button changes to a Commit button.
- Click Commit to add the Target.
Edit SharePoint Online (Graph API) Path
- Set up a SharePoint Online Target. See Set Up and Scan a SharePoint Online (Graph API) Target.
- In the Select Locations section, select your SharePoint Online Target and click Edit.
- In the Edit SharePoint Online dialog box, enter the site collection to
scan in the Path. Use the following syntax:
Description, Syntax and Example Scan all resources for the SharePoint Online web application.
This includes all site collections, sites, lists, list items, folders and files.
Syntax:
Leave Path blank.
Scan a site collection.
This includes all sites, lists, list items, folders and files for the site collection.
Syntax:
<organization>.sharepoint.com/sites/<site_collection>/:s
Example:
example.sharepoint.com/sites/operations/:s
Scan a site in a site collection.
Syntax:
<organization>.sharepoint.com/sites/<site_collection>/:s/<site>
Example:
example.sharepoint.com/sites/operations/:s/my-site
Scan all lists in a site collection.
Syntax:
<organization>.sharepoint.com/sites/<site_collection>/:s/:l
Example:
example.sharepoint.com/sites/operations/:s/:l
Scan a specific list in a site collection.
Syntax:
<organization>.sharepoint.com/sites/<site_collection>/:s/:l/<list>
Example:
example.sharepoint.com/sites/operations/:s/:l/my-list
A list item in a specific list cannot be individually added and scanned. You can only scan the entire list.Scan all folders and files in a site collection, or scan all list item attachments.
-
Syntax (for all folders and files in a site location):
<organization>.sharepoint.com/sites/<site_collection>/:s/:d
Example:
example.sharepoint.com/sites/operations/:s/:d
-
Syntax (for all list item attachments):
<organization>.sharepoint.com/sites/<site_collection>/:s/:d/Lists
Example:
example.sharepoint.com/sites/operations/:s/:d/Lists
- List item attachments are contained in the virtual "Lists" folder. To be able to scan them, ensure you have authenticated the SharePoint Online Target using client certificate and have granted the required SharePoint API permissions. See step 10 of Grant API Access.
- When probed in the UI, "Lists" is nested under the "File" folder.
Scan a specific folder in a site collection.
Syntax:
<organization>.sharepoint.com/sites/<site_collection>/:s/:d/<folder>
Example:
example.sharepoint.com/sites/operations/:s/:d/my-folder
Scan a specific file within a folder in a site collection.
Syntax:
<organization>.sharepoint.com/sites/<site_collection>/:s/:d/<folder>/<file>
Example:
example.sharepoint.com/operations/:s/:d/my-folder/my-file.txt
Recommended Least Privilege User ApproachTo reduce the risk of data loss or privileged account abuse, the provided for the intended Target should only be granted read-only access to the exact resources and data that require scanning. Never grant full user access privileges or unrestricted data access to any application if it is not required.
-
- Click Test and then Commit to save the path to the Target location.
Unsupported Types and Folders in SharePoint Online (Graph API)
ER2 does not support the following types and folders for the SharePoint Online (Graph API) Target:
- OneNote file types and folders. To scan these files and notebook folders, set up and scan the Microsoft OneNote Target instead.
- Personal sites.
Deleted SharePoint Online Sites
In SharePoint Online, deleted sites or site collections are retained for 93 days in the site Recycle Bin, unless deleted permanently. These deleted sites or site collections in SharePoint Online Targets are still discoverable by ER2, but will result in "HTTP 404" errors when attempting to probe or scan them.
SharePoint Online (Graph API) Remediation
Remediation can result in the permanent erasure or modification of data (and metadata). Once performed, remedial actions cannot be undone. Your organization's configured retention policies impact the behavior of the remedial actions applied to the current and historical versions of the match object. For more information, see Remediation Behavior in SharePoint Online Targets or contact the Ground Labs Support Team.
The following remediation actions are supported for SharePoint Online Targets:
-
Act Directly on Selected Location
- Mask all sensitive data
- Delete Permanently
- Quarantine
- Mark Locations for Compliance Report
- PRO Delegated Remediation
Unsupported Remediation Locations in SharePoint Online
The following locations and/or objects in SharePoint Online Targets are not supported for remedial actions that act directly on match locations:
- List items
- Site pages
- News posts
For more information on the unsupported locations for remediation for each Target, see Unsupported Remediation Locations by Target.
SharePoint Online (Legacy)
ER2 uses Azure ACS (Access Control Service) to access SharePoint Online. For new SharePoint Online tenants, using an ACS app-only access token is disabled by default and must be enabled manually.
From ER 2.14.0, you can use the Microsoft Graph implementation of Exchange Online by adding the SharePoint Online (Graph API) Target.
Overview
When SharePoint Online is added as a scan Target, ER2 returns all resources in the SharePoint Online web application. You can select specific site collections, sites, lists, list items, folders and/or files when setting up the scan schedule.
The instructions here work for setting up SharePoint Online as a Target.
To set up SharePoint Online as a Target:
- Enable SharePoint Add-in (for new SharePoint Online subscriptions only).
- Configure SharePoint Add-in.
- Set Up SharePoint Online as a Target.
To scan specific paths in a SharePoint Online Target, see Edit SharePoint Online Target Path.
Licensing
For Sitewide Licenses, all scanned SharePoint Online Targets consume data from the Sitewide License data allowance limit.
For Non-Sitewide Licenses, SharePoint Online Targets require Server & DB Licenses, and consume data from the Server & DB License data allowance limit.
See Target Licenses for more information.
Requirements
| Component | Description |
|---|---|
| Proxy Agent | 2.0.28 Agent and newer
Recommended Proxy Agents:
|
| TCP Allowed Connections | Port 443 for cloud services. |
Enable SharePoint Add-in
ER2 uses Azure ACS (Access Control Service) to access SharePoint Online. For new SharePoint Online tenants, using an ACS app-only access token is disabled by default and must be enabled manually.
For new SharePoint Online tenants, connect to SharePoint Online using Windows PowerShell and enable the SharePoint Add-in by running the following commands:
# Install the SharePoint PowerShell module
Install-Module -Name Microsoft.Online.SharePoint.PowerShell
# Set the administrator's account email address
$adminUPN="<full email address of a SharePoint administrator account>"
# Specify the organization's name to log into
$tenant="<name of your Microsoft 365 organization, example: mycompany>"
# Set the password in a secure prompt
$userCredential = Get-Credential -UserName $adminUPN -Message "Type the password:"
# Connect to the SharePoint server using the credentials provided
Connect-SPOService -Url https://$tenant-admin.sharepoint.com -Credential $userCredential
# Enable custom app (SharePoint Add-in)
Set-SPOTenant -DisableCustomAppAuthentication $false
For more information, see Granting Access Using SharePoint App-Only.
Configure SharePoint Add-in
Before adding SharePoint Online as a Target, you must register and configure the SharePoint Add-in for use with ER2. The registered SharePoint Add-in must have the required permissions to allow ER2 to authenticate and access (scan) the resources in your SharePoint Online environment.
ER2 uses Azure ACS (Access Control Service) to access SharePoint Online. For new SharePoint Online tenants, using an ACS app-only access token is disabled by default and must be enabled manually. For more information, see Enable SharePoint Add-in.
To configure the SharePoint Add-in for ER2:
Generate Client ID and Client Secret
You need to register the SharePoint Add-in to generate the client ID and client secret key which is required when setting up SharePoint Online as a Target.
To register the SharePoint Add-in:
- Log in to SharePoint Online and go to the AppRegNew form at
<site collection url>/_layouts/15/AppRegNew.aspx.
For example, https://mycompany.sharepoint.com/_layouts/15/AppRegNew.aspx. -
In the AppRegNew form, fill in the following fields:
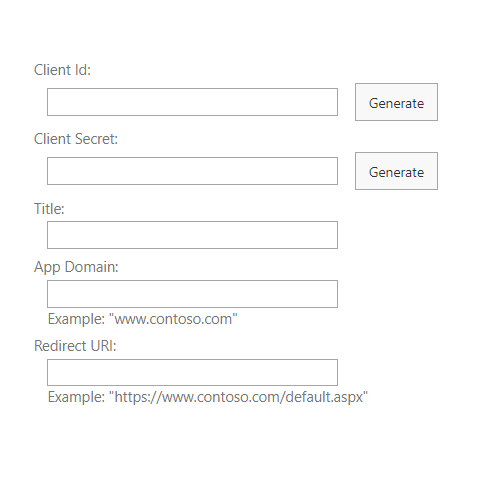
Field Description Client Id Enter a unique lowercase string, or click Generate to generate a client ID.
Example: 1234abcd-56ef-78gh-90ij-1234clientid
Client Secret Click Generate to generate a client secret.
Example: abcdefghij0123456789klmnopqrst0clientsecret
Title Enter a descriptive name for the add-in.
Example: Enterprise Recon SPO add-in
App Domain The host name of the remote component of the SharePoint Add-in.
Example: www.example.com
This is a compulsory field when registering the SharePoint Add-in, but is not required for scanning SharePoint Online Targets with ER2.Redirect URI The endpoint in the remote application or service to which Azure Access Control service (ACS) sends an authentication code.
Example: https://www.example.com/default.aspx
This is a compulsory field when registering the SharePoint Add-in, but is not required for scanning SharePoint Online Targets with ER2. - Click Create. The page reloads and displays the details of the newly registered SharePoint Add-in.
- Take down the Client ID (e.g. 1234abcd-56ef-78gh-90ij-1234clientid) and Client Secret (e.g. abcdefghij0123456789klmnopqrst0clientsecret) for the SharePoint Add-in. These will be required when you Set Up SharePoint Online as a Target.
Grant Permissions to SharePoint Add-in
- With your administrator account, go to the tenant administration site at
<tenant>-admin.sharepoint.com/_layouts/15/appinv.aspx
to grant permissions to the registered SharePoint Add-in.
For example, https://mycompany-admin.sharepoint.com/_layouts/15/appinv.aspx. - In the App Id field, enter the client ID (e.g. 1234abcd-56ef-78gh-90ij-1234clientid) for
the registered SharePoint Add-in and click Lookup.
See Generate Client ID and Client Secret - Step 4 for more information.
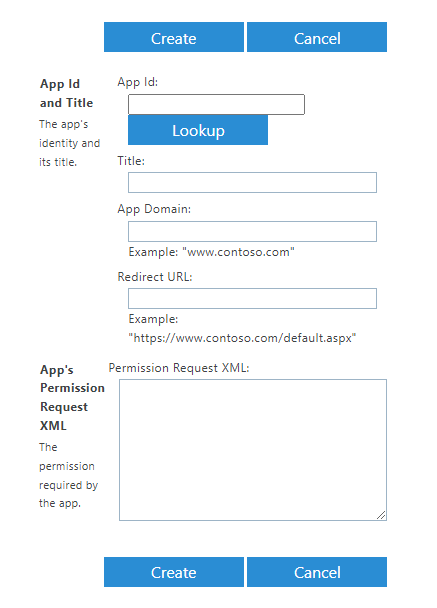
-
In the Permission Request XML field, enter the following permissions for the SharePoint Add-in:
<AppPermissionRequests AllowAppOnlyPolicy="true"> <AppPermissionRequest Scope="http://sharepoint/content/tenant" Right="FullControl"/> <AppPermissionRequest Scope="http://sharepoint/content/sitecollection" Right="Write"/> <AppPermissionRequest Scope="http://sharepoint/content/sitecollection/web" Right="Write"/> </AppPermissionRequests> - Click Create.
- You will be presented with a permission consent dialog. Click Trust It to grant permissions to the SharePoint Add-in.
- Go to the Site App Permissions page at
<tenant>-admin.sharepoint.com/_layouts/15/appprincipals.aspx?Scope=Web.
For example, https://mycompany-admin.sharepoint.com/_layouts/15/appprincipals.aspx?Scope=Web. - In the App Display Name column, look for the registered SharePoint Add-in (e.g. Enterprise Recon SPO add-in).
-
Take down the Tenant Id from the App Identifier value. This will be required when you Set Up SharePoint Online as a Target.
# App Identifier format: i:0i.t|ms.sp.ext|<client ID>@<tenant ID> i:0i.t|ms.sp.ext|1234abcd-56ef-78gh-90ij-1234clientid@12345678-abcd-9012-efgh-ijkltenantidWhere:- Client ID = 1234abcd-56ef-78gh-90ij-1234clientid
- Tenant ID = 12345678-abcd-9012-efgh-ijkltenantid
Set Up SharePoint Online (Legacy) as a Target
To add a SharePoint Online Target:
- From the New Scan page, Add Targets.
- In the Select Target Type dialog box, select Microsoft 365 > SharePoint Online.
- Fill in the following fields:
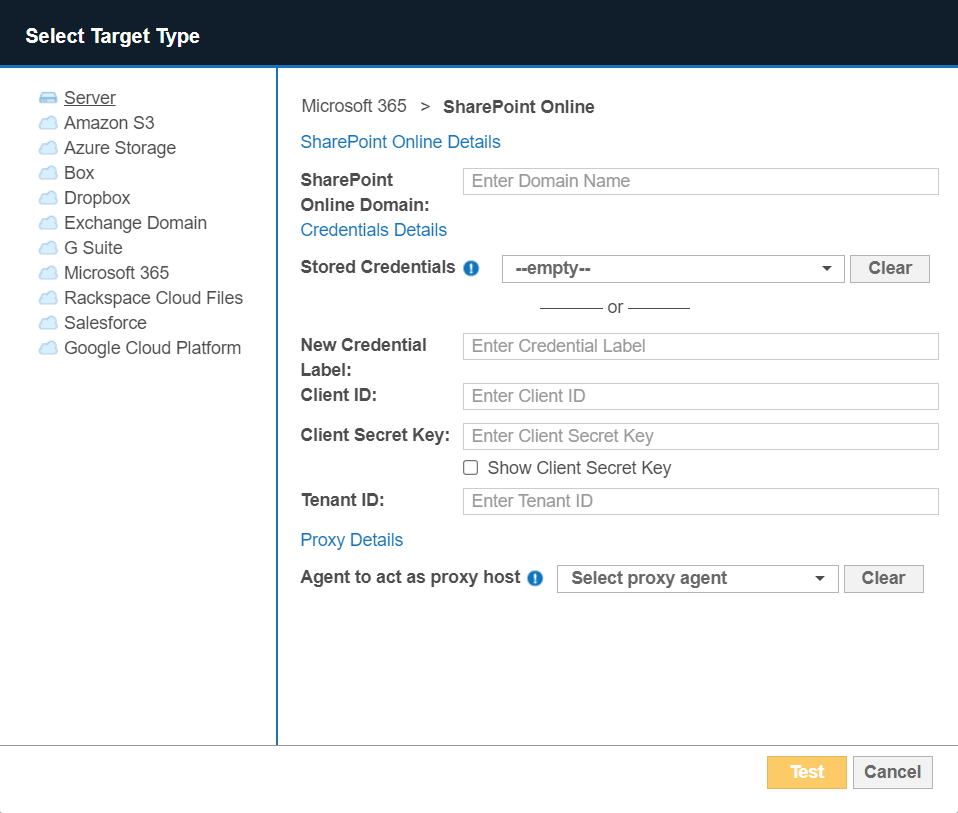
Field Description SharePoint Online Domain Enter your SharePoint Online organization name.
For example, if you access SharePoint Online at https://mycompany.sharepoint.com, enter mycompany.
New Credential Label Enter a descriptive label for the SharePoint Online credential set.
Client ID Enter the Client ID for the registered SharePoint Add-in.
Example: 1234abcd-56ef-78gh-90ij-1234clientid
See Generate Client ID and Client Secret - Step 4 for more information.
Client Secret Key In the Client Secret key for the registered SharePoint Add-in.
Example: abcdefghij0123456789klmnopqrst0clientsecret
See Generate Client ID and Client Secret - Step 4 for more information.
Tenant ID Enter the Tenant ID key for the registered app. Example: 12345678-abcd-9012-efgh-ijkltenantid
See Grant Permissions to SharePoint Add-in for more information.
Agent to act as proxy host Select a supported Proxy Agent host with direct Internet access. Recommended Least Privilege User ApproachData discovery or scanning of data requires read access. Remediation actions that act directly on supported file systems including Delete Permanently, Quarantine, Encryption and Masking require write access in order to change, delete and overwrite data.
To reduce the risk of data loss or privileged account abuse, the Target credentials provided for the intended Target should only be granted read-only access to the exact resources and data that require scanning. Never grant full user access privileges or unrestricted data access to any application if it is not required.
- Click Test. If ER2 can connect to the Target, the button changes to a Commit button.
- Click Commit to add the Target.
Edit SharePoint Online (Legacy) Path
- Set Up SharePoint Online as a Target.
- In the Select Locations section, select your SharePoint Online Target and click Edit.
- In the Edit SharePoint Online dialog box, enter the site collection to
scan in the Path. Use the following syntax:
Description, Syntax and Example Scan all resources for the SharePoint Online web application.
This includes all site collections, sites, lists, list items, folders and files.
Syntax:
Leave Path blank.
Scan a site collection.
This includes all sites, lists, list items, folders and files for the site collection.
Syntax:
<organization>.sharepoint.com/<site_collection>/:site
Example:
https://example.sharepoint.com/operations/:site
Scan a site in a site collection.
Syntax:
<organization>.sharepoint.com/<site_collection>/:site/<site>
Example:
https://example.sharepoint.com/operations/:site/my-site
Scan all lists in a site collection.
Syntax:
<organization>.sharepoint.com/<site_collection>/:site/:list
Example:
https://example.sharepoint.com/operations/:site/:list
Scan a specific list in a site collection.
Syntax:
<organization>.sharepoint.com/<site_collection>/:site/:list/<list>
Example:
https://example.sharepoint.com/operations/:site/:list/my-list
A list item in a specific list cannot be individually added and scanned. You can only scan the entire list.Scan all folders and files in a site collection.
Syntax:
<organization>.sharepoint.com/<site_collection>/:site/:file
Example:
https://example.sharepoint.com/operations/:site/:file
Scan a specific folder in a site collection.
Syntax:
<organization>.sharepoint.com/<site_collection>/:site/:file/<folder>
Example:
https://example.sharepoint.com/operations/:site/:file/my-folder
Scan a specific file within a folder in a site collection.
Syntax:
<organization>.sharepoint.com/<site_collection>/:site/:file/<folder>/<file>
Example:
https://example.sharepoint.com/operations/:site/:file/my-folder/my-file.txt
- Click Test and then Commit to save the path to the Target location.
Deleted SharePoint Online Sites
In SharePoint Online, deleted sites or site collections are retained for 93 days in the site Recycle Bin, unless deleted permanently. These deleted sites or site collections in SharePoint Online Targets are still discoverable by ER2, but will result in "HTTP 404" errors when attempting to probe or scan them.
SharePoint Online Remediation
Remediation can result in the permanent erasure or modification of data (and metadata). Once performed, remedial actions cannot be undone. Your organization's configured retention policies impact the behavior of the remedial actions applied to the current and historical versions of the match object. For more information, see Remediation Behavior in SharePoint Online Targets or contact the Ground Labs Support Team.
The following remediation actions are supported for SharePoint Online Targets:
-
Act Directly on Selected Location
- Mask all sensitive data
- Delete Permanently
- Quarantine
- Mark Locations for Compliance Report
- PRO Delegated Remediation
Unsupported Remediation Locations in SharePoint Online
The following locations and/or objects in SharePoint Online Targets are not supported for remedial actions that act directly on match locations:
- List items
- Site pages
- News posts
For more information on the unsupported locations for remediation for each Target, see Unsupported Remediation Locations by Target.
PRO This feature is only available in Enterprise Recon PRO Edition. To find out more about upgrading your ER2 license, please contact Ground Labs Licensing. See Subscription License for more information.